
On The Horizon | November 2020

For some of you, this is your first edition of On The Horizon, the monthly newsletter highlighting what’s coming down the pike for our teams at WesTech. Our priority is to keep you informed with each initiative and project. Here, you will find brief overviews of ongoing and upcoming projects. Our Support team and your Business Partners can fill in any gaps.
I know that (like each of your businesses) WesTech isn’t always easy to understand. So, I hope this can serve as a monthly “behind the scenes” peek to show what we are working on to become a stronger support system for you.
We have put together a short survey to get a bit more feedback on what you like and what you’d like to change regarding this newsletter and how we can improve communications. It’s only 7 questions, I promise it won’t take long!
Now let’s get to the latest at WesTech.
IN THIS EDITION
- Spamhaus Delisting
- OneDrive Migration
- Why Choose Lob
- Status Page Changes
- Message Central Progress
- Lytics Huddle Recordings
- Newsletter Survey

TRIED & TRUE PRACTICES FOR EMAIL DELIVERABILITY
Now that the Spamhaus block has been lifted, the Deliverability team will continue to work closely with the impacted businesses to warm IPs and build a positive reputation so that emails land in the inbox. At this time, over 90% of email traffic has migrated from the blocked IP space to SparkPost.
Due to our collective efforts, delivery has increased by 22% after making the needed changes to our mailing and list hygiene efforts. The focus now will continue to be strengthening each company’s reputation by following best practices and to support the push to implement engagement-based mailing strategies.
We know that these changes don’t have an end date, but we feel optimistic that incorporating the new practices will improve deliverability and allow your messaging to get into your customer’s inbox.
– Amanda Haughwout, Director of Email Deliverability
YOUR FILE STORAGE IS GETTING AN UPGRADE
Last month, we began the migration from Box to OneDrive and SharePoint for all of your documentation and file storage. The transition will be done in small groups and stages, organized by company and location, so if you share Box files with another group, there’s a chance you may not migrate at the same time. In that case, we recommend letting them know that shared files have moved. You will be notified both two weeks prior to your migration, and we’ll send a reminder the following week. Right now, everyone has access to their OneDrive and SharePoint accounts via your desktop app or OneLogin, so we also encourage you to begin exploring each before your migration occurs to help ease your transition.
PROGRESS SO FAR | At this time, the 14 West IT teams have migrated our files to OneDrive and we are currently in the process of moving the International groups over. Up next are the remaining 14 West teams, NewMarket Group, and Omnivista Health.
To learn how to work with OneDrive and SharePoint like a pro, you can find all needed training resources and information in the Microsoft 365 Evolve Workspace. If you would like a demo of each application, please reach out to help@14west.us.
– Lance Sturgis, Application Integration Specialist
LOB | THE FUTURE OF PRINT
With the implementation of Blueshift for Email and SMS notifications, we now have faster and more efficient communication. We know that print communications should be no different. That’s where our newest vendor, Lob, comes in.
We understand that it’s crucial to get in front of your customers from Day One in order to strengthen the quality of service you provide. Our previous system had an outdated content editor and a one-size-fits-all design, and we needed something that was able to be customized to suit your print needs. Although we’re in the rollout phase now, we’re excited to migrate each client over to Lob so that we can update dynamic content in real time, automate workflows, and have access to precise tracking and intelligent mailing metrics. We’re rolling this out for
Renewals first, but once the content has completely migrated over, we look forward to opening the platform to new print ideas.
– Jenelle Ketcham, Manager of Renewals
CUSTOMIZE YOUR STATUS PAGE COMMUNICATIONS
Most of you are well aware of our support application, Status Page, which serves as the centralized communication platform for our incident response management. The support systems in place have been setup to quickly detect errors in WesTech’s applications so you may notice an influx of emails from the trusty info@statuspage.io address. In an effort to lessen the influx of emails to your inbox, we wanted to remind you that the Status Page notifications are completely customizable on the Product level, so if you don’t need to receive error, maintenance, or incident communications on a certain product, you can take the following steps.
1. Head to https://14west.statuspage.io/
2. Click the blue button: “Subscribe to Updates”
3. Enter your work email and click “Subscribe via email”
4. This then takes you to a Preference Page where you can check boxes next to the Products and Services you wish to be notified about
5. Click “Save” at the bottom of the screen
– Randy Woolford, Enterprise Support Manager
LIGHTNING TALKS | NOVEMBER 17 & 18
UX Designers from both WesTech and Threefold are hosting a conference later this month aimed to help you improve the user experience on everything from your website to email to mobile that will enable you to drive your business forward. We know you’re busy, so we’re taking the “lightning” in Lightning Talks quite seriously by having each presentation take five minutes so that you’ll only need to spend 20 minutes each day. Speakers from internal teams will be sharing their UI/UX expertise, and we’re happy to announce that Paul Boag, CX Consultant with over 25 years of experience in Digital and Web Design, will be a guest speaker. You can find more information on the event here or sign up for each day below.
LIGHTNING TALKS
TUESDAY, NOVEMBER 18 | WEDNESDAY, NOVEMBER 19
BEGINS 9AM ET
MESSAGE CENTRAL UPDATE
You may have received a reminder from Daryl last month regarding our progress on sunsetting Message Central. In case you missed it, beginning Sunday, November 15, your role within Message Central will only allow you to view scheduled mailings, and all mailings* will need to be sent through Blueshift. Any updates to existing, scheduled mailings in Message Central should be requested through a Support ticket.
IRIS | Mailings created in IRIS are also going to be affected by our November 15 change. You may still use IRIS for tagging and split testing creation, but mailings created in the IRIS platform will no longer send. As for Lead Gen efforts, please contact the Support team for assistance with any mailings you need to send.
*As mentioned in previous communications, your API Triggered mailings (including Auto-Renew Notices and Credit Card Declines) and SMS mailings are an exception to this timeline.
GETTING THE MOST OUT OF THE DATA SCIENCE CAPABILITIES IN LYTICS
Our latest Lytics Huddles focused on their newest data science features: Laboratory, Content Classification, and Lookalike Models. If you weren’t able to watch them live, we’re sharing both recordings below.
LABORATORY SUMMARY | With Lytics Predictive Audiences, you now have the ability to build, fine-tune, troubleshoot, and validate these models on your own. You don’t need support from in-house data science or the Lytics team. With Lytics Predictive Audiences’ intuitive interface, you can. Watch here with access passcode: 6%c5?E8n
CLASSIFICATION SUMMARY | Much like we’ve done with lookalike models, we’re also updating the content area of Lytics’ dashboard with the addition of a Content Classification section to provide users with more transparency into how Lytics classifies content. This enhancement improves your visibility into content “health” and is a first step towards making content easier to curate and our content affinity engine easier to use. Watch here with access passcode: aZ9$8uj4
If you have any questions, please don’t hesitate to reach out to the Customer Intelligence team via our JIRA portal or customerintelligence@14west.us.
– Kathrin Simmons, CI Solutions Specialist
SURVEY REMINDER
You made it to the bottom, thank you for reading and scrolling through our updates! If you have five minutes, we would really appreciate your candid feedback on what you would like covered in these newsletters or communication pieces overall. Getting the right information to you as efficiently as possible is the ultimate goal, so please click here to complete the survey.
On The Horizon | October 2020

As we get closer to the end of 2020, my appreciation for our Business Delivery Team continues to grow and grow. When we designed the team in 2018, we knew there was real value there. But over a year like this one, with twists and turns around every bend, I truly believe they’ve been at the root of our ability to remain poised and productive. So, I want to kick this off with a quick acknowledgment of Kevin Woest and his team.
(Side note: I know Kevin has built some great relationships with many of you. If you haven’t gotten to know him and want to, I’d be really happy to introduce you.)
Anyway, their work has been more crucial than ever because we want to deliver consistent, reliable, world-class support and solutions to you. We can’t control everything. We can’t guarantee things won’t break. But a year like this one is all the evidence I need that we can overcome some incredible challenges together. We want to celebrate your wins, understand your problems, fix them quickly, get it right, and be a true partner. If we’re not doing that, we’re failing. And I really believe it all starts with communication. With that, here are the latest developments and insights from behind the tech curtain.
IN THIS EDITION
- Our Transition Off MC
- WMC Lead Gen is Live
- Status Page SMS
- AR Goes to Blueshift
Daryl

SUNSETTING MESSAGE CENTRAL
Earlier this week, you should have received a message from Daryl letting you know that as of yesterday, October 1, you will no longer be able to create mailings in Message Central. Any updates to existing scheduled mailings will require a Support ticket. This has been a huge project, so we want to make this transition for you as seamless as possible. If you are a Message Central user, here is an update on the offboarding process.
OCTOBER 1 | Your role within the system was changed, and while you will be able to login to Message Central to review and copy previously existing content, you will no longer be able to create new mailings. After October 1, any updates to existing, scheduled mailings in Message Central should go through a Support ticket.
SUNDAY, NOVEMBER 15 | All mailings* should be migrated out of Message Central and over to Blueshift. From this date on, your role will only allow you to view scheduled mailings. And all mailings will need to be sent through Blueshift. Any updates to cancel mailings in Message Central should be requested through a Support ticket.
*Please note, API triggered mailings and SMS mailings will be affected by the user update on Thursday, October 1 in the sense that you will not be able to create any new mailings within Message Central. However, these mailings have their own timeline and may not be migrated over to Blueshift by Sunday, November 15.
WE’RE LIVE | WMC LEAD GEN
The WesTech Marketing Cloud Lead Gen MVP is ready to go. If you are excited to get started, please reach out to your Business Partner or send an email to Katrina Kastendieck who can coordinate your setup.
With the Lead Gen MVP live, we continue to iterate on that product and will do so throughout the end of the year. In parallel, the WMC team continues to develop the MVP e-commerce components and the integration with payment processing. We are currently working closely with the Paygate and Advantage teams to test credit card payment processing through Spreedly for Worldpay and Vantiv. These capabilities are targeted to be completed in mid-October.
WHAT’S NEXT | Q4 Integrated Planning last month allowed us to identify internal cross-team dependencies and align through break-out sessions. The prioritized list of WMC capabilities were finalized this week and will be shared with you soon. Changes are inevitable, so any updates will be provided as we go through the 4th quarter. You’ll also receive announcements in the WMC application on any new capabilities as they are deployed, so watch this space.
We’d also like to give a big shout out to Banyan Hill for going live with a marketing effort using WMC, and following that up with another larger one very soon. Here’s to many more successful efforts.
-Judy Bluhm, Platform for User-Centric Marketing Applications Product Manager
EMAIL FAILED? SIGNUP FOR SMS
Earlier this week, there was a major outage within Microsoft that affected our workplace applications. You may have had trouble accessing Outlook, 365, Teams, or other tools that we’ve come to depend on. Since the outage wasn’t in our control, what was in our control was to communicate and inform you of the outage and the status of Microsoft’s systems. In order to ensure you have these updates (especially when our own email systems aren’t working), we recommend setting Status Page as a bookmark and to also sign up for SMS messaging (blue button at the top right of the page will lead you to that choice). When Outlook fails, SMS is the second best way to receive incident messaging.
If you have any questions about Status Page, please reach out to the Global Command Center.
-Tony Browne, Director, Support
AUTO RENEWALS ARE MOVING TO BLUESHIFT
Late last month, you may have heard from me regarding our plan to migrate AR notices (CIR) from Message Central to Blueshift that kicked off yesterday and should wrap up by Friday, December 11. Your mailings in Message Central will not be canceled until each campaign has been thoroughly tested, and please note that since this is a Blueshift API triggered mailing, the November 15 date will no longer apply.
FUTURE STATE | To push the necessary and legally required fields populated on the Auto-Renew notifications, the Renewals team along with Blueshift and Spine teams are building the payload to push the necessary fields from Advantage to Blueshift. The CIR340 Advantage process will be the key component needed for the payload build and new event triggered mailings in Blueshift. (the Cir340 is needed to populate the next rate).
TEMPLATE AND CAMPAIGN | Once content migration from Message Central to Blueshift kicks off, the Renewals team (with assistance from Blueshift) will build out dynamic templates with shared assets to reduce the number of setups for the two Auto Renewal sends. This will also include new campaign journeys for the timing of both email sends.
Your Renewals account manager will reach out soon with a list of requirements and will work with their contacts on a migration timeline. If you have any questions on the process or timelines for your own accounts, please reach out to me directly.
-Jenelle Ketcham, Manager, Renewals
On The Horizon | September 2020

We’re quickly approaching the final quarter of 2020. I know we’re all ready for this year to be over – for other reasons – but WesTech is committed to ending this year strong. As we dig into projects, complete tasks, and focus on the future of our systems, we’re dedicated to providing that strong support your businesses need to close out 2020 with confidence.
There are many people behind the scenes of projects and support who you don’t get to see or hear from every day, but I can honestly say they are a group that’s passionate to see you succeed. It’s important for us to understand every business in order to go well beyond “keeping the lights on.” I think the best way to continue our stronger ties is to keep learning from you. It may be because we had such an incredible Affiliate Spotlight presentation from Aaron DeHoog last month, but I want to keep learning about your businesses, your goals, your wins, and lessons.
So far, we have had invaluable sessions from Karen Reddel, Nate Hurd, Danni O’Dell, Karen Melchor, Aaron DeHoog. I’m happy to say APSI has continued this with their International clients.
Let me know if you’d like to be next.
For now, let’s dig into the latest at WesTech.
IN THIS EDITION
- PUMA Update
- OPIUM Downtime
- Free Trial Mandate
- Intelligent Automation on Evolve
- StatusPage
- Lytics Huddle
– Daryl

PUMA TEAM | WT MARKETING CLOUD UPDATES
The Westech Marketing Cloud (WMC) app is making progress! Watch this quick and informative WMC App Video to learn more about it.
LEAD GEN | The Lead Gen product is available to use, with several affiliates already getting comfortable creating Efforts, Creatives, and Journeys. If you have any questions or would like access, please reach out to mwilliams@14west.us and he can get you set up.
ECOMM | The eCommerce components are in development and will be available in the 4th quarter. If you are interested in being an early adopter for eCommerce, please reach out to jvirothaisakun@14west.us.
– Judy Bluhm,Platform for User-Centric Marketing Applications Product Manager
SCHEDULED OPIUM DOWNTIME | SEPTEMBER 26
You may have already received an email from Sarah Smiley this week, but we wanted to inform you that the PUMA team will be performing necessary maintenance to the OPIUM application and database on Saturday, September 26 at 3:00 AM ET. The scheduled downtime will last approximately two hours, during which time both the OPIUM application and order forms will be inaccessible. There will be no impact to any of our other applications or reporting during this time.
PLANNED WORK | This maintenance includes critical security patches to both the OPIUM application and database for increased performance, security and stability. This maintenance is necessary to ensure we are able to serve the best possible experience to our users, andcontinue to meet the security standards that are expected of our system applications at WesTech.
The entire PUMA team will be monitoring OPIUM and all of our other applications very closely during this timeframe to ensure orders are taken and processed once the system is back up. Please report any issues to Support so our teams can investigate.
SKILL UP IN INTELLIGENT AUTOMATION
Intelligent automation has been an ultimate goal for Michael Bresler and the Strategic Solutions and Automation team. With its help, we can catch mistakes earlier and better strategize for the future.
If you’d like to know more about intelligent automation or robotic processes, there is now an Intelligent Automation workspace on Evolve where you can learn anything from the basics, how to spot opportunities for bots in your workflow, and much more. If you have any questions on bots and automation, reach out to Michael here.
WHAT’S THE STATUS?
Last month, I sent a message regarding how the 14 West Support team is handling incident response and let you know what you can expect from us when you-know-what hits the fan with one of our systems.
Whether it’s Advantage, IRIS, OPIUM, FunnelCake, Blueshift, Signup App, Message Central, Middleware, Spine, Data & Analytics (formerly BI), and IT, you will get a communication from “noreply@statuspage.io” which is sent through our incident management application, StatusPage. What’s really great about StatusPage is that you can get a quick glimpse of our systems health dashboard that shows the current and historic health of the applications. If you haven’t done so already, please check it out here and subscribe to updates if needed.
If you have any questions regarding Support or StatusPage, please don’t hesitate to reach out to me directly.
– Tony Browne, Director of Support
ROADMAPPING WITH LYTICS
In our latest Lytics Huddle, Dillon Paul, Senior Product Manager, and Mark Hayden, VP of Product Management, from Lytics shared their Product Roadmap for the remainder of 2020.
In this huddle, they offered a sneak peek into the major product updates and design changes that are scheduled to be released later this year and early next year. If you’re interested in their vision for the future of Lytics, improvements to the workflow of the application, and more, please watch the recording here.
As always, if you have any questions about Lytics or would like to check the application out for yourself, please reach out to the Customer Intelligence team!
IMPERSONATION SPEAR-PHISHING ATTACKS
Here’s a term you probably haven’t heard about yet: spear-phishing. They’re targeted attacks that are typically more advanced and can be personalized in an effort to dupe the users into believing that they are reading legitimate messages.
Spear-phishing attempts come through every day into our environment, and many of you have also seen them. The most common – and most dangerous – are impersonation attempts, where an attacker will use a random email address (i.e. a name with random numbers @gmail.com or @outlook.com), change their display name (friendly from) to someone in the organization, and send a standard email with a greeting and small request. Some could ask for a cell number, changing direct deposit information in Ulti-Pro, or requesting gift cards to be purchased for co-workers or clients. Since most us only notice the name of the sender, it’s easy to miss that the email address. Here’s an example with the display name highlighted (note the email address to the right of it):
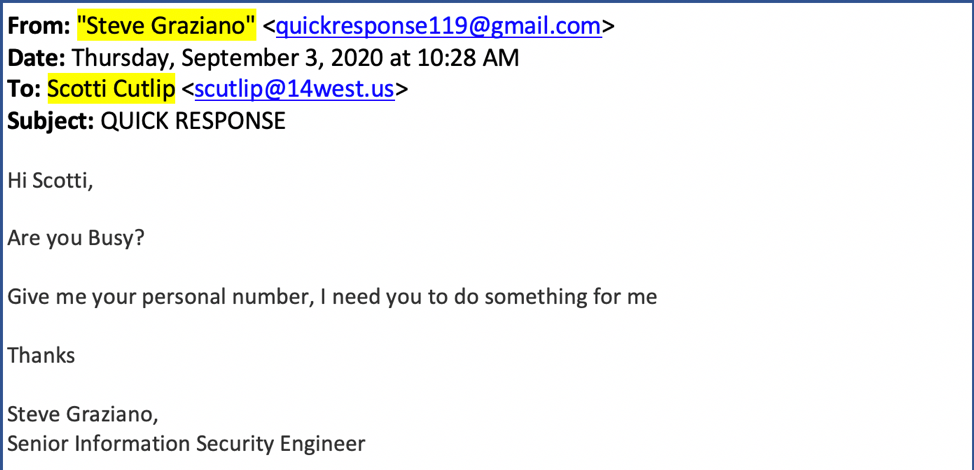
As we can see in this message, there’s a number of things that lead us to believe this is not a legit request:
- The email address “quickresponse119@gmail.com” does not match the email address for Steve Graziano, a 14 West employee, which should be “sgraziano@14west.us.”
- The subject line in all caps as well as other formatting and grammatical errors within the body of the message.
- Our company branded signature is not at the bottom of the email. The signatures are appended at the end of every email as they leave our email servers. Not everyone has one, but it’s something to look for. Alternatively, even with a company branded signature in an email, we still have to be on the lookout for these errors since signatures can be spoofed as well.
As with all emails you receive, always be aware that there’s a possibility it may not be from who it says it’s from. Spend an extra minute or two to investigate the email, using the above as an example, to determine if the communication is safe. If you notice that it is, in fact, a malicious attempt, then do not click anything in the email and do not reply. Immediately report the message using the Phish Alert button in your email client or forward the email to security@14west.us so we can investigate the origin and assign blocks through Mimecast.
If you have any questions regarding this information or would like you or your team to have a formal training on these possible attacks, please let us know and we will be happy to set it up!
– Steve Graziano, Sr. InfoSec Engineer
FREE & LIMITED TRIAL MANDATE CHANGES
In an effort to reduce chargebacks for subscription-related charges originating from free and limited trials, Visa and MasterCard released a mandate that provides more clear information to consumers and helps merchants fight against chargebacks that occur.
TYPES OF OFFERS AFFECTED | These are introductory offers and free trials which include bundle offers, offering premiums of components in packages, and book offers.
WHY CHANGE IS NEEDED | It is important for each business to adopt this mandate and make changes not only to be compliant with the card brands, but to lessen the chargeback rate and help with friendly fraud. This helps our ability to represent and win chargebacks, avoid class action lawsuits, and also provides optimal customer service by helping customers understand what they are signing up for from the start with ample communication on how to cancel.
EPP (Electronic Payment Processing team) is working closely with the affiliates and internal 14 West teams to ensure all needed changes are made. The majority of the changes required for this mandate is revolve around communication.
After working with Vantiv and Visa, we were able to get an extension to be compliant by mid- October, 2020. Vantiv also approved the notion that we don’t have to make changes to any of our e-comm systems that are sunsetting at the end of 2020. Everyone involved has been working diligently to meet our mid-October deadline and we look forward to implementing this mandate across the organization! If you have any questions about this mandate, please reach out to me directly.
– Elizabeth Cammack, Business Operations Analyst, FinTech
On The Horizon | August 2020

I’ll keep this short and sweet. Our roadmap for the second half of the year remains focused on the improvement and modernization of our products and services. A big part of this is lessening our dependency of Message Central, OPIUM, and other older systems and instead invest more of our time and effort in faster platforms like Blueshift and WT Marketing Cloud to drive value.
That’s our broader focus. And below, the team reports the nitty gritty on all the latest.
IN THIS EDITION
- Meet Tracky
- Lytics Huddles
- PUMA Team Updates
- Data: Drive with Confidence | New Course!
- Phish Alerts
– Daryl

INTRODUCING TRACKY | OUR DYNAMIC TRACK RECORD BOT
We’d like to formally introduce you to Tracky, our Track Record bot created by the GPS team. This powerful bot can manage the entire track record process by seamlessly doing the following:
- Track & execute published trade recommendations (subscriber alerts).
- Enter trades into the portfolio database & legal tracker spreadsheets.
- Send trade confirmation emails to financial gurus & editorial teams.
If you’d like to see Tracky in action, you can check out a demo of the bot entering a trade into Portfolio Tracker here. Currently, we run track record support for Money Map Press, but plan to roll this out to other clients in the near future.
– Tori Longo, Global Portfolio Services Product Owner
HOW TO REALLY PERSONALIZE YOUR CUSTOMER’S JOURNEY
The Customer Intelligence hosted two Lytics Huddles last month to cover everything you need to get started and using Journey Canvas (formerly Orchestrate). This journey-building feature allows you to deliver personalized marketing across channels without overlapping your targeting.
PART ONE | Craig Schinn from Actable, and Oxford Club’s TJ Tate present on how Oxford Club uses the Journey Canvas feature. This is a good example if you want to see Lytics in action and how to get the full scope of how to use Journey Canvas to your full advantage. Watch the recording here.
PART TWO | In this second journey-building installment, Craig dives deep into Journeys and their capability with Kim Toomey from Lytics. You will get an excellent walkthrough into the system and best practices when using the tool. Watch the recording here.
If you have any questions about Journey Canvas or getting started with Lytics, please reach out to the Customer Intelligence team here.
PUMA TEAM | WT MARKETING CLOUD UPDATES
LEAD-GEN | Beta testing has begun with NewMarket Group, Oxford Club, and Banyan Hill, as well as a demo of the product to Money Map. If you are interested in testing or going through a demo, please reach out to Matt Williams. You can read more about the MVP and Q3 priorities for Lead-Gen here.
E-COMM | We’ve put together the E-Comm MVP requirements after a great roundtable with Domestic businesses and are in the process of scheduling one with International affiliates. We’re planning to beta test with affiliates by September for features in the E-Comm MVP (except payment processing). We will develop and integrate payment processing as beta testing progresses, to give users time to get acclimated with WMC for creating order pages.
DATA: DRIVE WITH CONFIDENCE | NEW COURSE NOW AVAILABLE!
Our latest Data Literacy Awareness course will help you understand the importance of data literacy when it comes to your role within The Agora Companies. This interactive and exploratory course provides awareness of how data literacy impacts your role and sets expectations for a data literate workforce. We encourage everyone and anyone to enroll in the course in Evolve. Enroll directly from the Announcements page in Evolve.
For any questions is help accessing Evolve, please reach out to the L&D team here.
SKETCHY EMAIL? THERE’S AN APP (AND TEAM) FOR THAT
For as long as anyone can remember, emails have appeared in our mailboxes that we’ve either marked as spam into Junk E-Mail folders or deleted outright. They can range from annoying to potentially dangerous for users and the company as a whole. Our email security filtering system, Mimecast, keeps these emails out. However, the senders of these dangerous emails will always be looking for ways to circumvent mail filters.
No matter how good our defenses are, some will always slip through. That’s why we need to be prepared for when these cases arise by knowing what to look for and what we should be doing. We have a team who manages Information Security, but it’s everyone’s responsibility to understand how to report these emails and why.
SPAM VS. PHISHING
The first thing to recognize when receiving a message from an unknown external sender is whether the message is a “marketing” email (otherwise known as spam) or a phishing email with intentions of stealing information or compromising systems. Spam emails are not dangerous, just unwanted, and typically feature unsubscribe links to remove yourself from their lists. In the cases where an unsubscribe link is not present, or if they are requiring an email response to opt out of the lists, the best scenario is to block the sender through your preferred platform (Outlook, OWA, etc.) which will automatically send the messages to a junk email folder or deleted items.
PHISH ALERT PROCESS
Even with spam emails, there are cases where you see an email that appears suspicious and you don’t want to click anything in it (including unsubscribe links). For cases like this, we have had a system in place to report these emails to the InfoSec team. That system is known as the Phish Alert, which is located at the top of your received email messages. Here’s what happens once you click the Phish Alert button:
- The Phish Alert button sends an email tosecurity@14west.us and our PhishER compilation system, with the suspicious message as an attachment for review.
- The InfoSec team will then analyze the message and determine if it is safe to click or interact with.
- After analysis has completed, you will receive a direct response letting you know the results. If the responses appear automated, they both are and aren’t.We have crafted almost 50 different responses depending on the types of emails that come through. The PhishER system allows us to send these emails directly to the users, completely personalized, and addressing the reported message. It also gives us high levels of insight and reporting into the attacks we are receiving on a daily basis. While we can’t predict the attacks we are going to be hit with, PhishER allows us to be as proactive as possible and quickly quarantine malicious messages from mailboxes so our users don’t even have to read them.
PRACTICE MAKES PERFECT (OR JUST MORE PROACTIVE)
When you receive an email that you are suspicious of, the initial action should be to immediately report the message using the Phish Alert. This will notify the correct engineers on the InfoSec team quickly and ensure the issue is resolved.
Also, as you may have noticed at times during the year, we use the Phish Alert system to run simulated attacks. The best way to defend against attacks is to prepare our users with similar attacks and see how they respond. We are able to get full reports on clicks, responses, and many other categories so we can determine if further training is needed. While the simulations can be scary because everyone is receiving suspicious looking messages, they are nowhere near as scary as actual attacks that can hit all of our users within seconds.
UPCOMING TRAININGS AND WEBINARS
Our goal moving forward is to have everyone become more aware and mindful of the emails they are receiving. When something appears out of place or is obviously an attack, we will know exactly how to handle it. In the next month or two, the InfoSec team will be reaching out to all of the teams to setup virtual phishing webinars covering the information presented here, as well as more advanced techniques and examples. These webinars will be short but extensive, while offering time to ask as many questions as needed. If you would like to get a webinar setup immediately before we reach out, please contact the InfoSec team (security@14west.us) and we will be happy to set something up! And, as always, please let us know if you have questions regarding the information provided here or processes moving forward.
On The Horizon | July 2020

We’re coming off an exciting week for WesTech. For those who were able to attend the Deliverability Summit, I hope you found the sessions valuable. Please be on the lookout for a follow-up survey this week. One of our biggest goals in the Learning & Development space is to better measure the value of our programs from your perspective and use that insight to continue to improve. We can’t do that without your feedback.
For those who weren’t able to attend the sessions, you can find them here. We’re proud of the way this came out. We heard from a few people that it really helped to drive home the importance of this topic, and we hope to see that your teams are able to apply their new knowledge to your deliverability efforts.
Now, here’s what’s happening with the rest of WesTech.
IN THIS EDITION
- Shadow Apps
- Support Update
- ELI5 | Mimecast
- Data Literacy Initiative
- Strategic Solutions & Automation
- Deliverability Summit
- Vendor Score Card
-Daryl

FOUND A NEW APP? HERE’S WHAT YOU NEED TO DO
We’ve all done this. Sometimes you find an app that seems to be user-friendly, ties into your workflow nicely, and may even be free to use. And if it’s not free, you may even get your manager’s buy-in so that your team can use the tool. These are called “Shadow Apps,” which means they are not supported by IT and InfoSec at the company.
Although shadow apps can improve productivity and collaboration with little or no financial cost to your team or company, there are risks involved. Most importantly, you’re keeping the teams who work to keep our systems secure (within IT and InfoSec) in the dark. These applications may not have the right secure procedures in place, they may be blocked from our systems, or could alter the other systems we depend on. In some cases, we may already have this application on our systems or have an application that has the same capabilities, but require a bit of training.
We want to make sure you have the right systems in place to get your job done, so when you find a new application or have been using a tool that we did not provide, feel free to reach out to sysops@14west.us. We’ll do the research (if we haven’t already) so you don’t have to.
- 14 West System Operations team
THE LATEST FROM SUPPORT
Support has been focused on our continued evolution in both enhancements and purpose of the team. Here are the top initiatives we have for you.
INCREASED TRANSPARENCY | You should now be receiving monthly Support Summaries that offer a data-focused recap of the month. In addition to providing more visibility, we have worked to establish a consistent feedback loop with the Product teams. If you have any feedback or enhancement ideas, please continue to send them our way or reach out to me directly. As we continue to expand our vision and initiatives, receiving feedback is critical to our success and allows us to provide consistent and needed support.
UPDATED SLAs | We have made several adjustments to our existing SLAs and will send a document outlining all of our SLAs and the adjustments once completed. In the meantime, we’re pleased to let you know that we’ve decreased 6 of our existing SLAs, ensuring a quicker turnaround time for you. We’re also up and running with our Blueshift support and have now established the first of many Blueshift-centric categories. This is something we regularly keep watch of and will make further adjustments as we focus on our own in-house efficiencies.
- Brent Quickel, Manager of MarTech Support
ELI5 | MIMECAST
It has been over a year since we switched our email security gateway to Mimecast, so we wanted to give a refresher on what Mimecast has been doing and highlight one of its key features.
On average, Mimecast analyzes over 50,000 email messages per day for spam, misleading links, and phishing attempts. The protection this service offers has been a gamechanger and has kept large volumes of unwanted emails from reaching users. Email security will always be a fight because, as defenses improve, so do attacks that attempt to circumvent them. Mimecast has allowed us to be proactive and prepared for anything new we may encounter.
One way that we have adapted our security to confront current and future risks is by instituting Mimecast’s URL Protection policy, which could affect the links you create with false positives.
This policy has been active since we implemented Mimecast, and has provided an extra layer of protection and visibility for incoming emails. URL Protection applies to all emails that were sent to an internal mailbox from an external source (for example, from gmail.com to 14west.us). If the message meets that mail flow criteria, Mimecast will automatically scan the message for hyperlinks as it comes through. It will then “hijack” all links within the message and redirect them to a Mimecast landing page for the user to investigate.
The purpose of this landing page is to explain to the user that the link leads to an external source and shows the exact URL that the link is pointing to. A common practice of phishing emails is to provide a link that appears to go somewhere legitimate, but it instead leads to a malicious website used to steal credentials or force a download with payloads attached.
Spoofing a hyperlink is very easy, as I was able to do here in about 30 seconds: www.google.com. If you notice in that link, despite it saying “www.google.com,” the link actually points to “https://bing.com.” Had this message been sent from an external source, Mimecast would’ve hijacked the message and showed that it was pointing somewhere different than the message stated. Once you have reviewed the link and determined that the destination is what you expected and safe to visit, you can then continue to the original link that was sent without the Mimecast landing URL appended to it. While Mimecast does hijack the link at first, nothing about the link is changed if you decide to continue past the landing page.
Since we have a high volume of messages being sent from third party services and other external sources, false positives are inevitable with this system. To combat these false positives, we have a separate URL Protection “whitelist” that we can add domains and URLs into. This whitelist currently features all of our internal domains as well as a large number of known subdomains. Other URLs can be added into this list for business purposes if needed. In the event that you have an internal URL being hijacked that is causing business disruption, send an email to help@14west.us to create a ticket and it will be addressed quickly. We want URL Protection to function as much as possible, because unfortunately there are dangerous emails that will slip through the cracks of our filters. URL Protection gives that extra padding to ensure our users do not fall victim to these attacks and help increase awareness.
You can read more about URL Protection policy here.
If you have any questions about the URL Protection, or any other Mimecast policies, please contact the InfoSec team at security@14west.us and we will be happy to assist.
- Steve Graziano, Sr InfoSec Engineer
DATA: DRIVE WITH CONFIDENCE
The BI and L&D teams have been hard at work this past month launching our data literacy initiative called, Data: Drive with Confidence. We want everyone to understand data concepts and to have the confidence to read, work with, analyze, and argue with data.
As part of our awareness campaign, we have gone live with our first podcast series. Each episode digs into why data matters and how it can be instrumental for companies in the midst of digital transformation.
Each podcast is 15 minutes or less and perfect for in between meetings. If you haven’t gotten to listen in yet, you can start here.
WHAT DO YOU WANT TO HEAR NEXT? | We are taking suggestions for topics for our next podcast series to launch late summer. Provide suggestions and feedback here.
A QUICK NOTE | Data: Drive with Confidence podcast series is hosted on our new LMS platform, Evolve. If you have any questions about Evolve or have issues with access, please email evolve@14west.us and one of the LMS experts will quickly assist you.
COMING SOON | On demand Data Literacy learning modules for all new hires and all current employees, interactive micro-learning opportunities, and on demand tools training.
- Bojo Bauer, Manager, BI Customer Success
- Beth Oertel, Instructional Designer, L&D
STRATEGIC SOLUTIONS & AUTOMATION
Some of you already know about Michael Bresler’s latest initiative, Strategic Solutions & Automation. The goal of this team is to identify gaps and pain points, then turn them into opportunities to increase our value to your businesses.
For WesTech, we have found that there are certain ideas and areas to strategize that we may miss or have on the backlog. On many occasions, the answer could be intelligent automation (i.e. robotic process automation, chatbots, and/or business process automation), which is going to be a huge part of Michael’s work as he gathers more feedback on business processes and opportunities.
Working with Client Services, Michael will serve as a key listener to conversations with affiliates to truly understand pain points, and the solutions that could help their businesses. Michael will also be working in lockstep with Project Management as well as L&D to gather intel on the intake process, the strategy taken for projects, and to align with solutions needed in order to build our value.
GLOBAL PORTFOLIO SERVICES | The GPS team will continue to run under Michael, but the delivery and team lead will be Tori Longo as Product Owner. You can still depend on Lenny Kardelis as Track Record Analytics and Compliance Owner, Brian Buschling who is in charge of Track Record Support, and Morgan Cammack who handles Customer Success.
If you have any questions about Strategic Solutions & Automation make sure you reach out to Michael directly.
DELIVERABILITY SUMMIT
Thank you for those who were able to join at least one of the virtual sessions for our first ever Deliverability Summit last week. For those who didn’t, we have each session located in the Email Deliverability Workspace here. If you have any issues with access, please reach out to the L&D team here.
The presenters and teams involved in this event are strong thought leaders on the subject of Deliverability today, so we hope you found the sessions insightful and possibly even had a few aha moments that you can apply to your own business strategy.
For any questions or feedback on this summit, you can reach out to me directly.
- Matt Estes, Manager of Learning & Development
VENDOR SCORECARD | GETTING TO KNOW YOUR SOURCES
With ThoughtSpot, you can now analyze mailing data down to the individual subscriber. This level of granularity allows us to ask questions of our data that were not possible to answer before, and all within seconds of asking.
If you are already in ThoughtSpot, you’ll notice that a pinboard called the Vendor Scorecard has recently been shared with you. This pinboard helps you evaluate new lead sources by highlighting engagement rates during subscribers first days on your list. The pinboard looks at the unique percent of engaged subscribers during their first seven days on file to their first thirty, so that you can decide early on if a source of names is going to be good for your business.
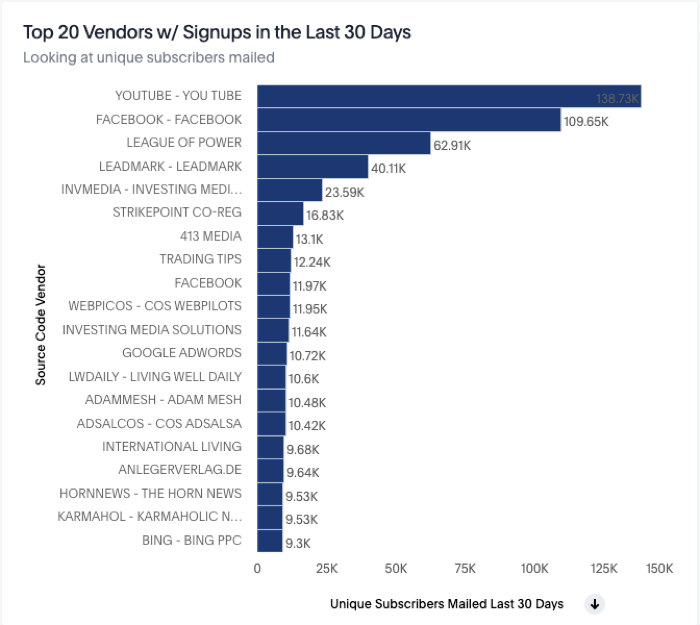
For more information, or if you are not a ThoughtSpot user, please reach out to BI at intel@14west.us and we’ll get you started.
- Rachel Kozloski, ThoughtSpot Product Owner
On The Horizon | June 2020

Our goal is to be that reliable source that allows you to keep your business running and to continue to be that technical support that you can depend on. I understand and know that businesses are under incredible stress, now more than ever. And we’re committed to relieving some of that. We want to be great partners to you.
To do that we have to be on the same page. To help ensure that we are, our Business Partners have created a survey to help measure our progress when it comes to general alignment with your needs and delivering solutions that satisfy or exceed your expectations. The results are used to drive the development of our strategy, goals, and roadmaps. So although I know you’re tight on time, we want to remind you to click here to complete the survey. This shouldn’t take more than 5 minutes.
Now let’s get to the latest.
IN THIS EDITION
- WesTech Satisfaction Survey
- Deliverability Summit
- ELI5 | InfoSec
- Speak Data with Us
- Business Partner Initiatives
- Command Center Update
- Motivation from a Former Running Back
-Daryl

LEARNING FROM THE EXPERTS ON EMAIL DELIVERABILITY
To help drive deliverability, improved customer relationships, and improved monetization, we’ve put together our first ever Deliverability Summit.
DELIVERABILITY SUMMIT
MONDAY, JUNE 22 – FRIDAY, JUNE 26
1 x 1-HOUR SESSION / DAY | 12:00 PM – 1:00 PM ET
We’ll be working with our own internal teams as well as industry experts from SparkPost, Blueshift, and Email Ninjas. If you can’t make it or would like to refer back to the sessions, please note that they will be recorded.
ELI5 | WHAT IS CCPA AND WHY DOES IT MATTER?
In this month’s “Explain Like I’m 5,” the Info Sec team is covering the importance of the California Consumer Privacy Act (CCPA). While working in the publishing space – and especially tech – it’s crucial for you to understand how it affects us.
The California Consumer Privacy Act (CCPA) is a new government regulation very similar to GDPR (General Data Protection Regulation for the EU). While GDPR focuses heavily on the customer’s right to opt-in to any sort of solicitation or marketing, CCPA focuses on a consumer’s right to opt-out of it.
CCPA’s main tenets are the ability for a consumer to request “do not sell” of their information towards any scenario that the business currently engages in. Additionally, the consumer has the right to request how their information is being sold or monetized, how the data is stored and transferred (similar to GDPR), and a full report of what personally identifiable information (PII) a business holds on that consumer.
Similar to GDPR, the fines for CCPA can be quite heavy for those who violate. While GDPR has the general rule of up to four percent of gross revenue of the parent company for violations, CCPA’s violations can be more granular and equally as painful depending on the circumstance. CCPA fines can be up to $750 dollars per consumer, and up to $7500 per incident per person. This can quickly add up, depending on the number of incidents that are incurred.
A RECAP…
Should we care about CCPA? Yes.
Is CCPA like GDPR? Yes, very similar. GDPR is about opting in, CCPA is about opting out. Both are about protection of privacy data.
Are the fines heavy? Absolutely.
What should we be concerned with as a business? Responsibly handling customer or employee PII (name, address phone number, email address) according to CCPA and GDPR guidelines.
Should we care about vendors who store information? Yes.
As we continue to work towards compliance, having a good understanding of the basics can go a long way. For additional details on CCPA, please feel free to contact security@14west.us.
- Paul Xu, Vice President, Information Security
BECOMING BETTER ALIGNED WITH YOUR BUSINESS
The Business Partners have developed two major resources that allow WesTech to keep our fingers on the pulse when it comes to supporting your companies.
CLIENT ADVISORY BOARD | We held our first CAB meeting last month where we were able to take the time to sit down (albeit virtually) and discuss the bigger strategic goals you have. Most importantly, we were able to start the process to learn the why behind your goals so that we can develop and streamline the support we provide. We came out of it with a long list of key action items and great ideas that we aim to get started with immediately, if not already.
In order to keep each other on track and committed, a major action item for WesTech is to develop breakout seasons for Data, Product, and Deliverability to clearly understand the clients’ why and how. These will involve microdiscussions and full transparency around what affiliates are trying to achieve which will help us prioritize. The ultimate goal: 100% alignment between WesTech and every affiliate. Looking forward to the next one and to keep this momentum going.
LAUNCH-READY INITIATIVE | When you are preparing for a sizable launch, we want to tap in the right resources (Support, IT, Advantage, Ecomm, Messaging, Deliverability, Fintech) to make sure they can proactively monitor performance of their systems and become hyper-aware of any issues that may arise. So far, we’ve tested this with most affiliates and we were able to fine tune the processes needed, and look forward to many more successful launches. If you have any questions on this process, please let me know.
- Doug Broujos, Chief Client Officer
OUR LYTICS HUDDLE WENT FULLY VIRTUAL
For our latest Lytics Huddle, Craig Schinn, co-founder of Actable, Drew Lanenga from Lytics, and CI’s very own Chris Laun presented on data science and machine learning. The decisions marketers have to make in each of your highly-segmented campaigns are challenging to manage. Fortunately, you have a number of tools at your disposal to help reach the best customers and prospects at the right time. Watch the recording here.
A WORD FROM BRIAN MITCHELL
WesTech was given an exciting opportunity yesterday to virtually host former NFL running back turned motivational speaker, Brian Mitchell, for an inspiring transformative talk. Never a group to shy away from hearing a different perspective on the qualities of hard work and dedication, we were happy to hear from Mr. Mitchell and found his presentation so insightful that we wanted to share the recording with you as well.
Click here to watch. If you have any issues with access, please reach out to Jenny Realo.
On The Horizon | May 2020

Mine is going to be a short and sweet update this month. This week has been a difficult one. On Tuesday evening and early Wednesday morning we let go of a number of valued people including a member of our executive team, CIO Reid McLaughlin. It never feels good to let good people go, but we felt it was our responsibility to become more efficient to remain in line with the things we can’t control right now. And I truly feel that the adjustments made have enabled us to move closer to each of your businesses. Our roadmap to the improvement and modernization of our products and services remains intact.
Over the next several weeks, our executive committee is going to continue to work to ensure we are running a lean and effective operations outfit. In the process we’ll use one common denominator to determine where we focus our energy and resources and that is value – the value we can deliver to you, your people, and your customers. Along the way, we will be looking to you for your insight and communicating about these efforts here in On The Horizon each month. If you feel you have any questions or need additional insight on projects we have open with you, you can still depend on the Business Partners for this. But please know that my “door” is always open.
With that said, here’s the latest from around WesTech.
IN THIS EDITION
- MarTech team update
- L&D office hours
- PUMA team update
- ELI5 | InfoSec
- Lytics 101 trainings
- Marketing in the Age of COVID-19
-Daryl

MARTECH TEAM | COMBINING FORCES
The Messaging Product (Message Central, Newshift) and Customer Intelligence (Lytics) teams are now working more closely together as one MarTech team. While the two teams continue to work more closely together, the CI team is taking what they learned from driving the adoption of Lytics and applying that towards our current efforts of onboarding users onto Blueshift.
BLUESHIFT ADOPTION | The state of this project is rapidly evolving with data integration, and we are working to provision all needed instances this month. From there, we expect the nature of our work to change as we stand up advanced features in the system and ease out of the affected businesses becoming de-listed with Spamhaus. Getting over these next few hurdles will allow us to move a lot faster, taking time to migrate and then to go back and optimize campaigns.
- David Schweinfurth, Director of MarTech
SYSTEM-SPECIFIC OFFICE HOURS
If you’re not sure if a question is ticket-worthy or you just need someone to talk you through a workflow, there just might be an office hour for that. The L&D team has set up dedicated time for WesTech-supported systems so that you can sign on and get the help you need.
For ease of access, the Zoom link is the same for each of the office hours listed below, so keep this handy for when you need to join.

ALIGNMENT WITH THE PUMA TEAM
For those who I haven’t been able to meet yet, the IRIS, Sign-up App, OPIUM, and Funnelcake teams have merged together into one cohesive unit – the PUMA team (Platform for User-centric Marketing Applications). Combining these teams will enable us to streamline the backend services we offer while sustaining legacy systems.
API FIRST | We’re building out an environment that improves efficiencies and speed using APIs you can easily plug into. The good news is that IRIS+ was built using this “API First” approach, and our first milestone to target completion of the Lead Gen MVP this quarter.
FUNNELCAKE | As you know, Funnelcake has performance issues, the root cause being Magento – the software the order form application was built on. Our strategy right now is to pull Magento out of the system and to build this product on high performance technology, delivering results in the fastest, most cost-effective way.
- Judy Bluhm, PUMA Product Manager
ELI5 | DATA ENCRYPTION
The InfoSec team wants to explain a few of the “more techy” concepts that you may hear a lot, but never fully understand. In this month’s “Explain Like I’m 5,” Paul goes into data encryption and why it is crucial to data privacy.
You’ve probably heard this at some point or another, Encrypt this, encrypt that, hash this hash that.
But what exactly does it mean and why should I know?
Let’s start with encryption.
Simply put, it’s taking a piece of data, running it through some sort of function/formula/algorithm and making that data unreadable to an outside party who shouldn’t have access to that data.
For example, if you assigned a number to each letter of the alphabet (i.e. A = 1, B =2, C=3) and want to write the word “DOG” but wanted to encrypt this word using your new numerical formula, it would turn into “4,15,7” ( D = 4, O = 15, G = 7). Now you can tell the recipient of your message that your “key” is just a sheet of paper with A-Z with their respective numbers assigned to it. Now only you and the recipient know how to read the messages. Although overly simplified, the basic points are the same for any encrypted message. You can “hide” all of your data in plain sight. It’s important to note that encryption provides privacy of your data, but it also allows the data to be returned to its original form when you have the “key.”
Hashing is very similar to encryption, the big difference being there is no key, and the data can never be returned back to its original form. It can never be “unhashed.” So why is this needed?
One key point about hashing is that, depending on the algorithm you are using, you should be able to create a unique hash for every single word or combination of words you choose. No two hashes should ever be alike, which can be very powerful to protecting our data. This is especially important when we are talking about sensitive data.
Take user passwords, for example. In the encryption scenario, if a system encrypted all of the passwords, an engineer or hacker could somehow steal the key and decrypt those passwords again. But if those passwords are hashed, you cannot decrypt them or regain the original passwords. This makes hashing very useful for protecting things that should never be touched (i.e. passwords, timestamps, digital signatures).
As we move deeper into our dependence on the digital world, everything we do will consist of some type of encryption or hashing. Our data should be encrypted most of the time, and the rest of the time hashed. This protects us and gives us peace of mind.
LYTICS 101 TRAININGS
The Customer Intelligence team (now part of the MarTech team) wants to remind you that they offer Lytics 101 trainings that cover the basics of the CDP. Whether you’re new to the company, have been here for a while but need a refresh or just curious to learn how we can get a deeper understanding of our customers, this training is a great learning opportunity.
If you have any questions about Lytics, reach out to the CI team.
MARKETING IN THE AGE OF COVID-19
We developed a conversation that included a panel of marketing experts from Banyan Hill, The Oxford Group, and NewMarket Group to dissect recent successes they have found in the midst of a pandemic. Craig Schinn of Actable brought his expert knowledge on how to leverage tools like Lytics and Blueshift to add to your strategy. We were pleased to have Brian York joined to offer his insight and host the event.
On The Horizon | April 2020

At the beginning of Week 4 of quarantine, and I know I’m not alone when I say that March was really difficult, and April is looking the same. I mentioned last month that change is constant, but I didn’t expect something so abrupt as a pandemic.
We’re in a strange new world right now. Nate Hurd said it best when he spoke to my teams in last month’s Affiliate Spotlight. He said that this pandemic is the type of event that makes you take a step back and think about what really matters. What matters to me is your business. I’ve spent the last three weeks trying to invite myself onto as many calls and zooms as I can manage and consuming as much content as humanly possible. And every day I’m reporting back to the team.
Our team needs to see what’s happening in your business. And I really need to know from you whether we’re hitting the mark and supporting you in the ways you want and need to be supported. So here are the updates for this month. Any and all feedback is welcome.
IN THIS EDITION:
- TrackMate Survey
- Scam of the Month
- No Dev is an Island
- L&D takes on Montana
- A Warning About Cyber Thieves
- Remotely Interested
- The Latest from Support
-Daryl

A QUICK FAVOR FROM THE TEAMS AT THREEFOLD
You may have already heard a bit about this tool, but in the coming months, we hope to work more with you to improve tracking and receive better analysis on your campaigns. Trackmate was built to give marketers great insight into the performance of campaign funnels through improved tracking and analysis. To ensure Trackmate suits your needs, the team at Threefold wants to hear from all affiliate marketers. Click here to tell them what matters most to you!
–Brendan Tobin, UX Designer
STARTING OUT WITH SLACK?
Slack has quickly become an essential way to keep in touch with our teams as we adjust to remote working. I wanted to share this quick guide that includes best practices and tips to getting the most out of this application. If you have any issues with Slack or messaging your coworkers, please email us at help@14west.us.
–Lance Sturgis, Application Integration Specialist
OUR FIRST HACKATHON | READY FIRE HACK
Last month we partnered with the experts at Red Hat to hold our inaugural Agora Hackathon deemed Ready Fire Hack, held at City Garage. This gave Developers and UX Designers from both WesTech and Threefold the rare opportunity to work together under the same roof to build out solutions to challenges specific to the Agora businesses.
Themes from the business problems focused on customer experience, compliance, and content engagement. We think it’s safe to say that the event was a major success, as each of the teams came up with incredible ideas that have real potential to become smart solutions for your businesses. But we had to choose one winner – the team who call themselves Your Form.
Your Form chose to focus on the issue that many of you have experienced – making long copy work on mobile. Working with The Oxford Group’s Brian Kehm, who happened to be at City Garage that day, they were able to better understand the workflow from an editorial perspective. Working with call center data, breaking up the content into digestible sections on a content management system, and fully understanding how to get the most value from the copy from a small screen were crucial to coming up with a solid plan… and winning the competition.
Elliot Sneeringer wrote up his takeaways for a recent WestWord post, which you can read about and watch a video of the event here.
SCAM OF THE MONTH | COVID-19
At this point, we’ve all been able to settle into this routine of working from home, but it’s very important to remember that scammers are too. While we are busy worrying about where to find the next roll of toilet paper or how to keep our kids from killing each other, they are busy coming up with new ways to capitalize on this pandemic. As important as it is to keep our hands adequately cleaned, we must remain extra vigilant when it comes to coronavirus scams. Here are just a couple of methods that scammers have quickly started to use.
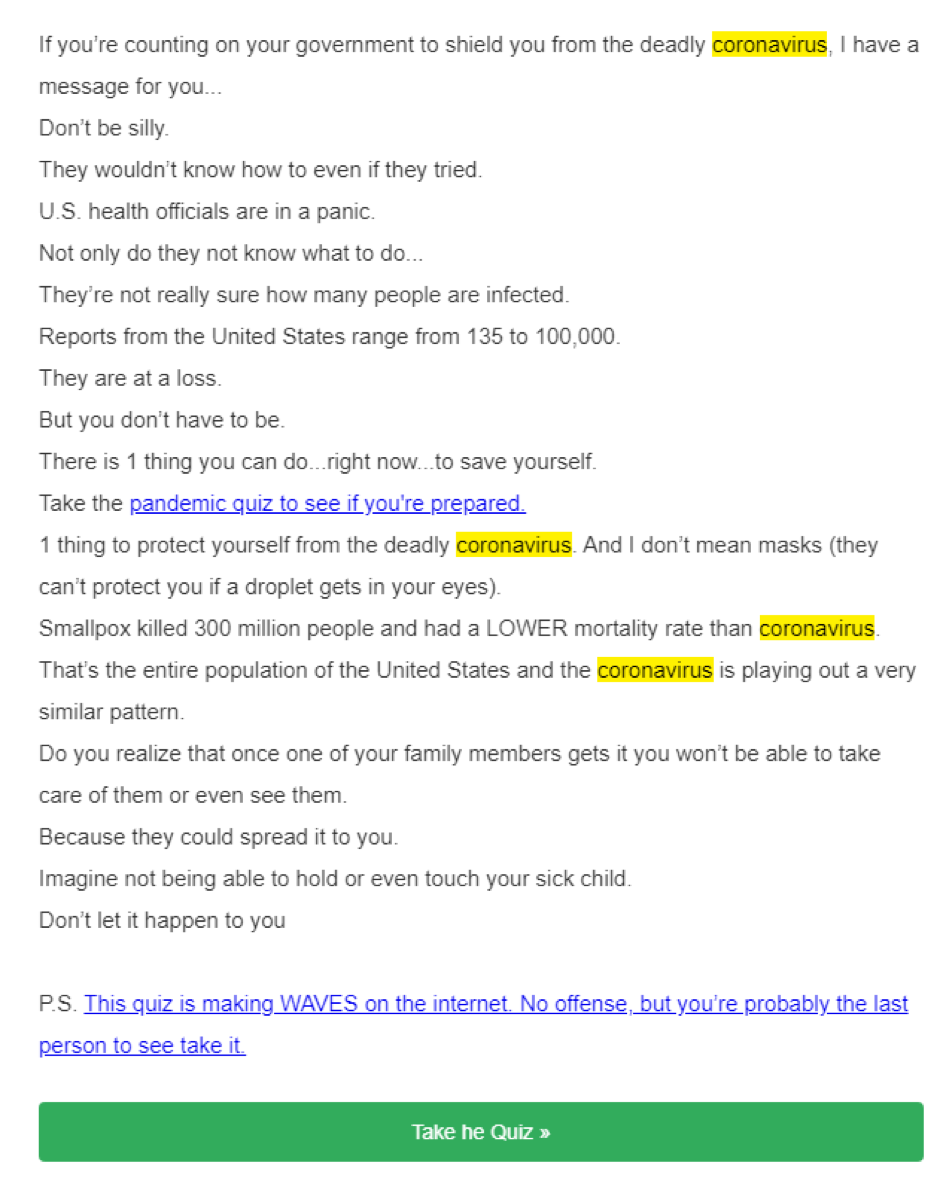
PHISHING SCAMS | This one involves a quiz. Just giving it a quick glance, it’s obvious that this isn’t something you want to click. These links could take you to a fake page to grab your credentials or could prompt a download to release malware – which is much worse. There are other ones out there that are doing things such as asking you to confirm you are not infected or showing you the latest active tracker map. As with all phishing scams, DO NOT CLICK ANY LINKS unless you are 100% sure you know where it came from. And even then, I would ask someone first.
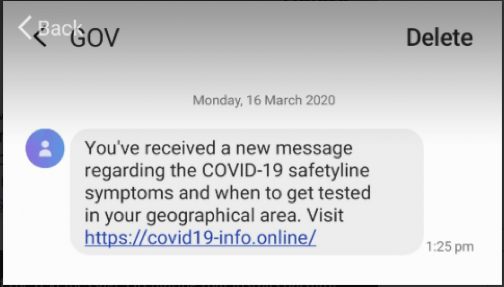
TEXT MESSAGES | This is another easy one, which involves receiving random text messages that tell you how to get tested or information on the virus. These are generally malware-based and are more dangerous than the ones you see in the emails.
Other usual suspects include social media and phone calls. As with emails and text messages, if you receive links in social media messages, invites to pages tracking the virus, or information on the virus, you should stay away. Even if the message came from someone on your friends list, it could generally mean they were hacked as well. Make sure you reach out to that person to confirm first.
As always, if you ever have any questions or are not sure please reach out to security@14west.us. We are always happy to help. Please stay safe and vigilant everyone!
-Paul Xu, VP Information Security
L&D WAS CALLED WESTWARD
We’ve just finished up with a unique collaborative project with NewMarket Group to train their new call center representatives in Billings, Montana. In just three weeks, we were able to provide the needed materials and train their agents specific to NewMarket’s policies and procedures in addition to the usage of Advantage.
It was a solid team effort working with NewMarket Group, but we couldn’t have done it successfully without such a receptive group of people who work at the call center.
-Laura Appel, Senior Training Partner
THE LATEST FROM SUPPORT
On the Products end, we are now handling all Global Porfolio, BI (Tier 1), EPP (Tier 1), Funnelcake, and Blueshift tickets. We’ve introduced a dedicated triage to ensure consistent communication and customer experience for your businesses. We’re keeping up with Product teams by holding regular feedback meetings and delivering product reports. Working more closely with the Business Partners to coordinate regular touchpoints with you has also helped improve visibility to ensure we get your Product issues resolved as quickly as possible.
– Tony Browne, Director of Support